- VMware Technology Network
- :
- Cloud & SDDC
- :
- vCenter
- :
- VMware vCenter™ Discussions
- :
- how to check who assigned\deleted permission on an...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
how to check who assigned\deleted permission on an object in vcenter inventory
Hello!
I'm trying to figure out how to find who assigned\deleted permissions in VC's inventory.
I use VCSA 6.5 build 7312210 and 7515524
I read William's article https://www.virtuallyghetto.com/2017/06/auditinglogging-vcenter-server-authentication-authorization-...
A big problem that whenever you create\delete pemission, related Event shows that vcenter solution user did this and not a real user. (Screenshots in the article show the same behaviour).
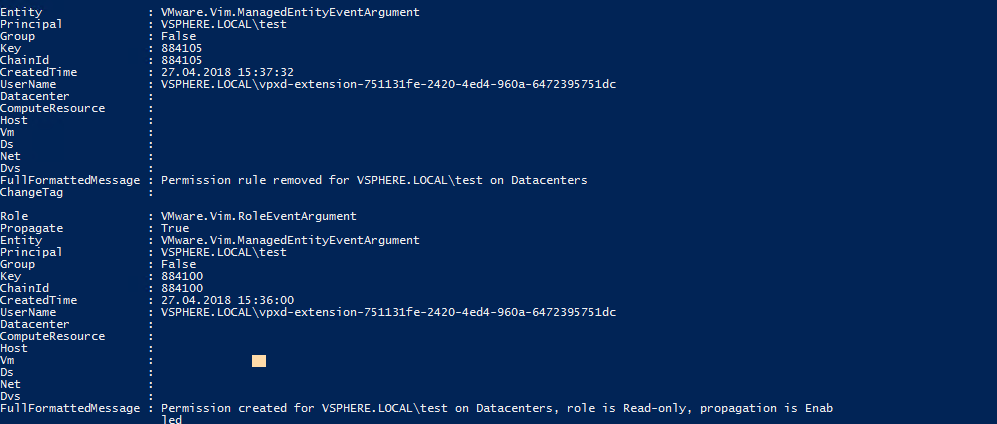
Here the example
1. Permission for user 'test' created on vcenter level and Read-only role is assigned
2. Then this permission is removed
Actually this was administrator@vsphere.local user who did this.
What I checked:
1. vpxd.log shows nothig for this action
2. SSO logs show nothig also.
3. Gettings events using PowerCLI shows the same
Any suggestion how can I get real user who assigned\deleted permissions?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Do you have logs being captured by vRLI? If so, that should have it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I do, but Loginsight shows the same events and it also can show me the same logs which I can read manually ![]()
I did another test with domain users
here evets from vRLI
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
But actually I don't send VCSA logs like vpxd and others to loginsight.
However SSO and vpxd logs show nothing for this actions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hmm, yes I see. It may not be possible to recollect in that case if there's solution user substitution. Is this something you know of, mikefoley?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Have you configured syslog on vCenter to send to Log Insight? (Not the vpxd logs, actually setting it at the VAMI)
You'll get the vCenter Events, the same content you see in the event viewer in the web client.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As pointed out, the source logs don't seem to contain this information (check Finikiez's post at the top).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok, I've double checked the vpxd.log and it seems I missed some lines when checked it before.
2018-04-27T17:29:04.875+03:00 info vpxd[7F79F9602700] [Originator@6876 sub=vpxLro opID=21231cff-af64-4799-8bfc-1dc5e777b12c-cd] [VpxLRO] -- BEGIN lro-1529846 -- AuthorizationManager -- vim.AuthorizationManager.fetchUserPrivilegeOnEntities -- 522facb3-f8d0-e789-c380-2fc1968c463b(5243dfe1-44ac-57f6-e479-022835c2959a)
2018-04-27T17:29:04.875+03:00 info vpxd[7F79F9602700] [Originator@6876 sub=[SSO] opID=21231cff-af64-4799-8bfc-1dc5e777b12c-cd] [UserDirectorySso] GetUserInfo(VSPHERE.LOCAL\test, false)
2018-04-27T17:29:04.909+03:00 info vpxd[7F79F9602700] [Originator@6876 sub=[SSO] opID=21231cff-af64-4799-8bfc-1dc5e777b12c-cd] [UserDirectorySso] GetUserInfo(VSPHERE.LOCAL\test, false) res: VSPHERE.LOCAL\test
2018-04-27T17:29:04.910+03:00 info vpxd[7F79F9602700] [Originator@6876 sub=[SSO][GroupcheckAdapter] opID=21231cff-af64-4799-8bfc-1dc5e777b12c-cd] [FindAllParentGroups]
2018-04-27T17:29:04.930+03:00 info vpxd[7F79F9602700] [Originator@6876 sub=AuthorizeManager opID=21231cff-af64-4799-8bfc-1dc5e777b12c-cd] [Auth]: User VSPHERE.LOCAL\test
2018-04-27T17:29:04.930+03:00 info vpxd[7F79F9602700] [Originator@6876 sub=vpxLro opID=21231cff-af64-4799-8bfc-1dc5e777b12c-cd] [VpxLRO] -- FINISH lro-1529846
2018-04-27T17:29:04.934+03:00 info vpxd[7F79FA29B700] [Originator@6876 sub=vpxLro opID=21231cff-af64-4799-8bfc-1dc5e777b12c-f1] [VpxLRO] -- BEGIN lro-1529847 -- AuthorizationManager -- vim.AuthorizationManager.hasUserPrivilegeOnEntities -- 5239060e-38e5-8cbc-6a78-1a5c049e362c(526eb8b0-e98c-8a9d-34d8-a6f78e5bde99)
2018-04-27T17:29:04.934+03:00 info vpxd[7F79FA29B700] [Originator@6876 sub=[SSO] opID=21231cff-af64-4799-8bfc-1dc5e777b12c-f1] [UserDirectorySso] GetUserInfo(VSPHERE.LOCAL\Administrator, false)
2018-04-27T17:29:04.976+03:00 info vpxd[7F79FA29B700] [Originator@6876 sub=[SSO] opID=21231cff-af64-4799-8bfc-1dc5e777b12c-f1] [UserDirectorySso] GetUserInfo(VSPHERE.LOCAL\Administrator, false) res: VSPHERE.LOCAL\Administrator
2018-04-27T17:29:04.976+03:00 info vpxd[7F79FA29B700] [Originator@6876 sub=[SSO][GroupcheckAdapter] opID=21231cff-af64-4799-8bfc-1dc5e777b12c-f1] [FindAllParentGroups]
2018-04-27T17:29:05.030+03:00 info vpxd[7F79FA29B700] [Originator@6876 sub=vpxLro opID=21231cff-af64-4799-8bfc-1dc5e777b12c-f1] [VpxLRO] -- FINISH lro-1529847
2018-04-27T17:29:05.033+03:00 info vpxd[7F79FA826700] [Originator@6876 sub=vpxLro opID=21231cff-af64-4799-8bfc-1dc5e777b12c-ff] [VpxLRO] -- BEGIN lro-1529848 -- AuthorizationManager -- vim.AuthorizationManager.removeEntityPermission -- 52246423-9537-1d0a-738c-ec90594dc7d2(5273d5ec-ad08-80ca-2c37-cbddb57dbdb7)
2018-04-27T17:29:05.033+03:00 info vpxd[7F79FA826700] [Originator@6876 sub=[SSO] opID=21231cff-af64-4799-8bfc-1dc5e777b12c-ff] [UserDirectorySso] GetUserInfo(VSPHERE.LOCAL\test, false)
2018-04-27T17:29:05.071+03:00 info vpxd[7F79FA826700] [Originator@6876 sub=[SSO] opID=21231cff-af64-4799-8bfc-1dc5e777b12c-ff] [UserDirectorySso] GetUserInfo(VSPHERE.LOCAL\test, false) res: VSPHERE.LOCAL\test
2018-04-27T17:29:05.074+03:00 info vpxd[7F79FA826700] [Originator@6876 sub=vpxLro opID=21231cff-af64-4799-8bfc-1dc5e777b12c-ff] [VpxLRO] -- FINISH lro-1529848
It's not so obvious but seems that vpxd checks user who tries to remove permission before removing permissions for another user.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So if vpxd.log is capturing it, you need to install the vRLI agent on your vCSA and configure an agent group which has that definition (from the vSphere content pack). It should then parse all those log streams.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I guess that it's better to fill up a feature request to make this process much easier in future ![]()
Thanks )
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Agreed, although good luck with that ![]()
Feature request form is here, BTW: https://www.vmware.com/company/contact/contactus.html?department=prod_request