- VMware Technology Network
- :
- Digital Workspace
- :
- Horizon
- :
- Dynamic Environment Manager
- :
- Starting a Disabled Service
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We had attempted to create a logon task that called on a .bat file to start a disabled service. The contents of the .bat are:
sc config EmOpti.Service start= demand
net start EmOpti.Service
It seems though that regular users, who have just user access locally, are getting denied. Apparently starting a service requires elevated rights.
Is there a better way to go about this? I was thinking of using the "Privilege Elevation" piece of UEM (9.2.1), since that's what it sounds like it's designed for, but, haven't touched it yet. I'd really rather not leave this service enabled by default on our parent image.
Thanks in advance.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yeah, task triggers by UEM 'Logon Tasks' will not be elevated because of security and logon processes that run in a different context.
The easiest workaround is to let the script be triggered by a shortcut in the 'Startup' folder. This shortcut can be created by UEM.
Another workaround is to use the [HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] location to trigger the logon task.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi epa80,
Indeed, non-admin users can't typically start or stop services.
UEM's privilege elevation can definitely be used for this, but for the script-based approach that would entail allowing users to run sc.exe and net.exe with elevation (well, just sc.exe, as you can also use that to start a service :-), regardless of the additional arguments. That means that they could stop and start (and remove, and configure, and...) any service.
In a future product version we might add some more granularity in the configuration of privilege elevation, but for now you would need to create a dedicated executable that changes the service state and starts it. You can then just configure that particular executable for elevation.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So perhaps I am misconfiguring the Privilege Elevation setting(s).
As of this morning we were not using this any way. So 1st step, I selected the Global Config for the PE setting, enabled it, and added my test group as the condition. This group has a user I am trying to get this service start to work with. I save that, I do not check another of the boxes in that window:
Then, I create a PE job as follows: I made the type path based, I selected the full path for sc.exe, and made the condition the same group as above:
Am I missing anything else? When we login to a VM with a user in that group, the logon task still bombs out. The bat file is updated as:
sc config EmOpti.Service start= demand
sc start EmOpti.Service
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yeah, task triggers by UEM 'Logon Tasks' will not be elevated because of security and logon processes that run in a different context.
The easiest workaround is to let the script be triggered by a shortcut in the 'Startup' folder. This shortcut can be created by UEM.
Another workaround is to use the [HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] location to trigger the logon task.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you please expand on this?
I'm essentially trying to do the same thing as epa80; I've created a shortcut within UEM to kick off a batch file within a VDI session to change an existing service from Disabled to Automatic, and then trying to start the service. However, its not working for an ordinary user, but if I log in with an account that has Admin rights to the system it works.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi GTO455,
To allow a non-admin user to perform such an action, you would need to use UEM's Privilege Elevation feature. Specifically, argument-based privilege elevation, so you can elevate cmd.exe, but only if it runs to launch your startfwder.bat script.
So, something like this:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
GTO455,
I know it was a little confusing for us the first time we used UEM's privilege elevation feature. Have a look at these pages in this order.
Page 1. Configure Privilege Elevation
Page 2. Enable and Configure Privilege Elevation
Page 3. Configure Applications for Privilege Elevation
Attached is a screenshot of what we have configured as far as what page 2 describes.
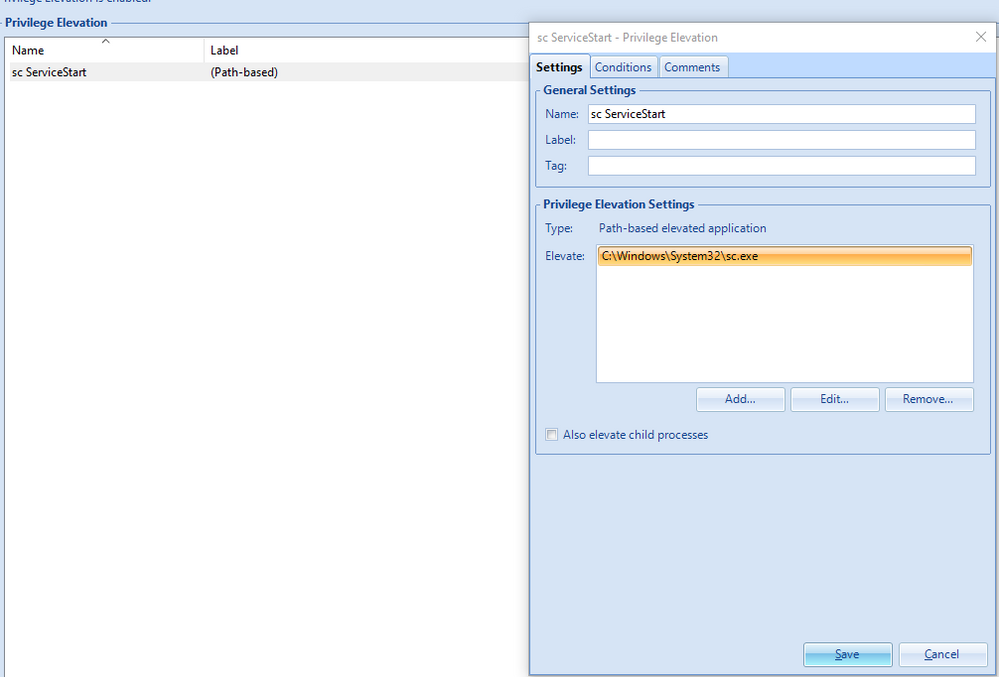
Another attachment is a screenshot of the application we are allowing to elevate, SC.exe (related to Page 3.)
Keep in mind, on top of all of this you still have to create that shortcut to actually run your bat file to launch (or whatever app shortcut you are needing to launch).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the additional info, agalliasistju!
Just wanted to point out that in your example, you're configuring elevation for sc.exe in general, which means that all use of sc.exe will be elevated. As of UEM 9.4 we support argument-based privilege elevation, which you can use to limit elevation to only certain specific service-related actions, if you so require.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
UEMdev that's a great feature! We'll need to get to that version, currently on 9.2.1 🙂
That feature makes a lot of sense and helps with my concerns for security. Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Guys,
Thanks for the replies. I am using Hash and Publisher-based Privilege Elevation in a couple of other scenarios and it works well. I never thought to try Argument-based.
UEMDev, I tried your suggestion but it still doesnt seem to be working.
Contents of startfwder.bat"
sc config Forwarder start= auto
net start Forwarder
I can see the batch file run at login, but it appears the "SC" and "Net Start" commands within the file is generating an Access Denied error.
So I tried creating another Argument based PE containing SC.exe and the arguments following the command above and that doesnt seem to be working either.
Within the VM if I manually try to run the file as an ordinary user or user with Admin rights on the VM (in a CMD window-non elevated) it fails with the following:
[SC] OpenService FAILED 5:
Access is denied.
System error 5 has occurred.
Access is denied.
If I elevate CMD with Admin user account on the VM and manually run the file, it runs successfully.
Any other suggestions to try?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi GTO455,
I just played around with this myself, and it initially didn't work for me either. Then I remembered that you need to actually run the command that's configured for argument-based elevation with its full path, so in your case C:\Windows\System32\sc.exe, rather than just sc. Even though "bare" sc will be found in the path, the way that that information comes through in UEM does not allow us to match that back to the configured path...
Could you please try it like that?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Maybe something totally different but you could change permissions on services so that a user is able to start the service itself, even if it is disabled.
We did this for one specific service which we wanted to start using a script with a delay.. Little bit more cumbersome but also an option ![]()
https://blogs.msmvps.com/erikr/2007/09/26/set-permissions-on-a-specific-service-windows/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
UEM Dev,
I'm afraid its still not working for me. Maybe I am missing something. To recap I have
An Argument Based Privilege Escalation entry in UEM:
A Shortcut in UEM:
And a Batch File with the following content:
C:\Windows\System32\sc.exe config Forwarder start= auto
C:\Windows\System32\net.exe start Forwarder
Is that right? After login I see the service is still set to Disabled. The only Condition Sets I have are that the file exists in the directory specified.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
GTO455
I think you said in an earlier comment that you see the batch file run during login??? If you do actually see it run I'm not sure why it's not working for you at this point, but if you don't see it, are you clear on your CONDITIONS that are configured to trigger it?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi GTO455,
I would suggest to create argument-based privilege elevation settings for both C:\Windows\System32\sc.exe config Forwarder start= auto and C:\Windows\System32\net.exe start Forwarder. With your current setup, you can't control whether the launch of your script through its shortcut will actually call cmd.exe with its full path (which is a requirement for argument-based elevation to work.)
It might also work if you change your shortcut definition to launch C:\Windows\System32\cmd.exe /C C:\Windows\Scripts\startfwder.bat...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Yes, it runs and I have the output sent to a log file. I'm getting an Access Denied error when SC and NET try to run
[SC] OpenService FAILED 5:
Access is denied.
The only CONDITIONS I have configured in UEM is that the File or Folder exists (set in both Shortcut and Privilege Escalation):
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
GTO455 I guess to beat a dead horse...
In UEM 9.2.1 I have 3 different places where Conditions need to be met for my PE to work correctly.
1. Globally
2. On the EXE that CAN be elevated
3. On the Shortcut that is launched
(I think this one is self explanatory)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi UEMdev and agalliasistju
Thanks, I have tried all of the suggestions in this thread and still isn't working. I'm beginning to think someone screwed with the Local Policies on this image in a way that I can't unscrew it. There is no reason why this shouldn't be working.
The script is executing fine, but the SC and NET commands within the file are not executing within the CMD window.
I even tried
- Creating a shortcut to the file, going into Advanced Properties of the file, having it run as Administrator and then pointing UEM to launch the shortcut
- Converting the bat file to an exe file and using a path-based Privilege Escalation rule
I did find a workaround here for the service itself, but I haven't tried it yet.
Thanks to all who tried to help. If you've got something else in mind I'm up for the challenge, but I'm all out of ideas.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi GTO455,
Sorry to hear that it's still not working for you. Just to make sure, I just tried it (with another service), and it does work for me.
Which version of UEM are you on? Is there anything interesting in the log file? If you configure a "normal" executable like regedit for elevation, and enable the Ask user to elevate message in the global configuration, do you see that message, and does elevation work?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello UEMdev,
Sorry I havent replied sooner, I've been working on other tasks.
On your suggestion, I tried approaching this issue from another path. I tried using the programs exe to stop the service (there is a variable to allow that), but I can't get it to launch from the startup folder at login.
I have the command from the shortcut in UEM outputting to a text file and it says: "Forwarder: Unable to stop the service: Access is denied."
If I change the setting to "Ask user to Elevate" I am not prompted as a standard user (and it fails), but if I log in with an account with Administrator rights to the desktop I am prompted, allow it to run and it works.
However, with the Privilege Elevation for cmd.exe and the programs exe, I can get it to run a different way. If I let the login complete, open a CMD window (unelevated) and run it from there, it works, and a an entry in the Windows Event Log is generated noting the UEM privilege elevation.
So it appears to be something with the Startup folder/Startup that is preventing it from executing.
I even tried going the Local Security Policy and setting all of the UAC settings to their defaults and it made no difference.
I don't see any errors in the log file, and like I mentioned, it does work if I run the command manually.
We're running UEM 9.4, App Volumes 2.14 and Horizon 7.5