- VMware Technology Network
- :
- Digital Workspace
- :
- Horizon
- :
- Horizon Desktops and Apps
- :
- Wildcard certificate and Horizon 7 - failed to get...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Wildcard certificate and Horizon 7 - failed to get certificate chain
Hi,
i'm trying - desperatly - to install a wildcard geotrust certificate on our horizon connection server, but it fails with;
WARN (1494-1408) <Thread-1> [KeyVaultKeyStore] (NetHandler) Failed to get certificate chain for: "vdm"
WARN (1494-1408) <Thread-1> [KeyVaultKeyStore] (NetHandler) Certificate chain not found for alias: vdm
The certificate in question is a valid, wildcard GeoTrust SSL CA - G3 certificate, with the following properties:
Version V3
Signature algoritm: sha256RSA
Signature hash: sha256
Public key: RSA (2048 bits)
friendly name: vdm
The certificate chain in the certificate mmc, shows OK.
The private key is exportable, and security is set to full control of the service user running the services. (plus system and admins).
There is only this certificate with the friendly name "vdm"
It feels like the intermediate and/or root is not in the jre servers' trusted certificate store, so i tried to create a truststorefile.key and load it with a locked.properties file, but that didnt help.
Trying to access the admin site (https://localhost/admin) gives the error "ERR_SSL_VERSION_OR_CIPHER_MISMATCH" with Chrome and "SSL_ERROR_NO_CYPHER_OVERLAP" with firefox.
Any tips/ideas/suggestions would be very appriciated!! ![]()
/Chris
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Chris,
We have a very similar issue.
* Were you able to solve your issue?
* Where did you see the "WARN (1494-1408)" errors? Are there logs that I should be looking at that I have no seen. Please advise.
thx. EJ
======
Product:VMware Horizon 7.x
Product version:7.0.2 - 4356666
Issue description:After updating cert, "View Connection Server" no-longer reachable via https. SSL Cert for "View Connection Server" will expire
Cert appears to match with prior cert relevant fields and does show as "Certificate Status: This certificate is OK."
(Cert is from Network Solutions)
Followed instructions on:
1 Add the Certificate Snap-In to MMC
2 Import a Signed Server Certificate into a Windows Certificate Store
3 Modify the Certificate Friendly Name "vdm"
========
Chrome receives:
-----
This site can’t provide a secure connection
123.abcd.com uses an unsupported protocol.
ERR_SSL_VERSION_OR_CIPHER_MISMATCH
Unsupported protocol
The client and server don't support a common SSL protocol version or cipher suite.
-----
IE11 receives:
-----
This page can’t be displayed
Turn on TLS 1.0TLS 1.1and TLS 1.2 in Advanced settings and try connecting to https://123.abcd.com again. If this error persists it is possible that this site uses an unsupported protocol or cipher suite such as RC4 (link for the details)which is not considered secure. Please contact your site administrator
-----
**** Replacing old cert and changing Friendly Name to "vdm" corrects issue but old cert will expire.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
!
I may have an answer:
In our case the issue was an option left default when "Create Custom Request..." was selected from the certificate mmc.
On the 'Custom Request' screen of 'Certificate Enrollment', select "(No template) Legacy key" from the 'template:' field.
(Do not leave as the default, "(No template) CNG key")
After making this one change, generating a new .req file and using it to reissue a cert., all worked as expected via normal processes.
Documentation for VMware Horizon 7 version 7.0
Please see attached PDF and jpg for more detailed info.
Also note that VMware recommends generating SSL certificates using the following utility/configuration file/script. However, I have not tired this method.
======
Notes:
Server OS = Server 2012 R2 Standard
Cert type = Wildcard (*)
SSL Security Provider = Network Solutions
======
Please let me know how it goes.
thx. EJ
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Step 10 on this page seem to confirm it:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It's weird though. I've installed versions 5 and 6 and was able to use a standard wildcard I used for other services. Now, for whatever reason, this no longer works. I really hope they fix this in the very near future!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I had the same issue
And I resolved it by selecting the check box to make the certificate Exportable
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
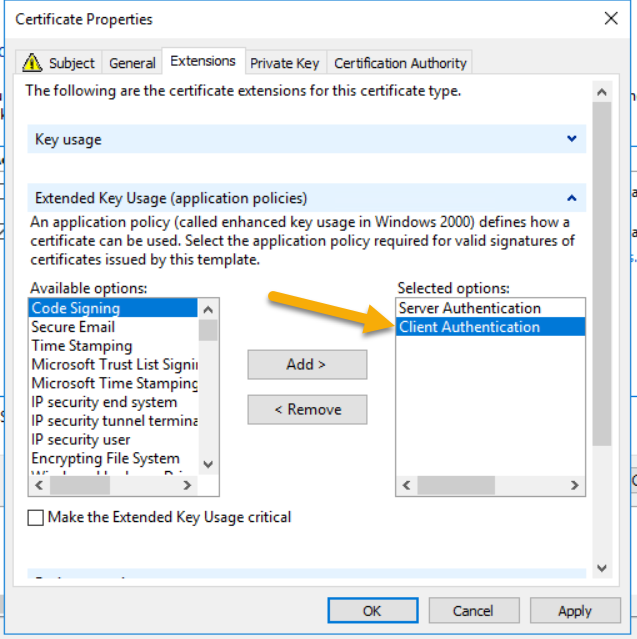
I used the active directory enrollment polity, selected Web Server.
after adding the subject name, entering vdm for friendly name, my template was missing the Client Authentication for the extended key usage. For the private key tab, check the box to make the private key exportable.
Click ok and Enrole!
Make sure to delete or remove the friendly name "vdm" from any old cert.
Restart Services and voila!