- VMware Technology Network
- :
- Networking
- :
- VMware NSX
- :
- VMware NSX Discussions
- :
- Re: guest introspection use case?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
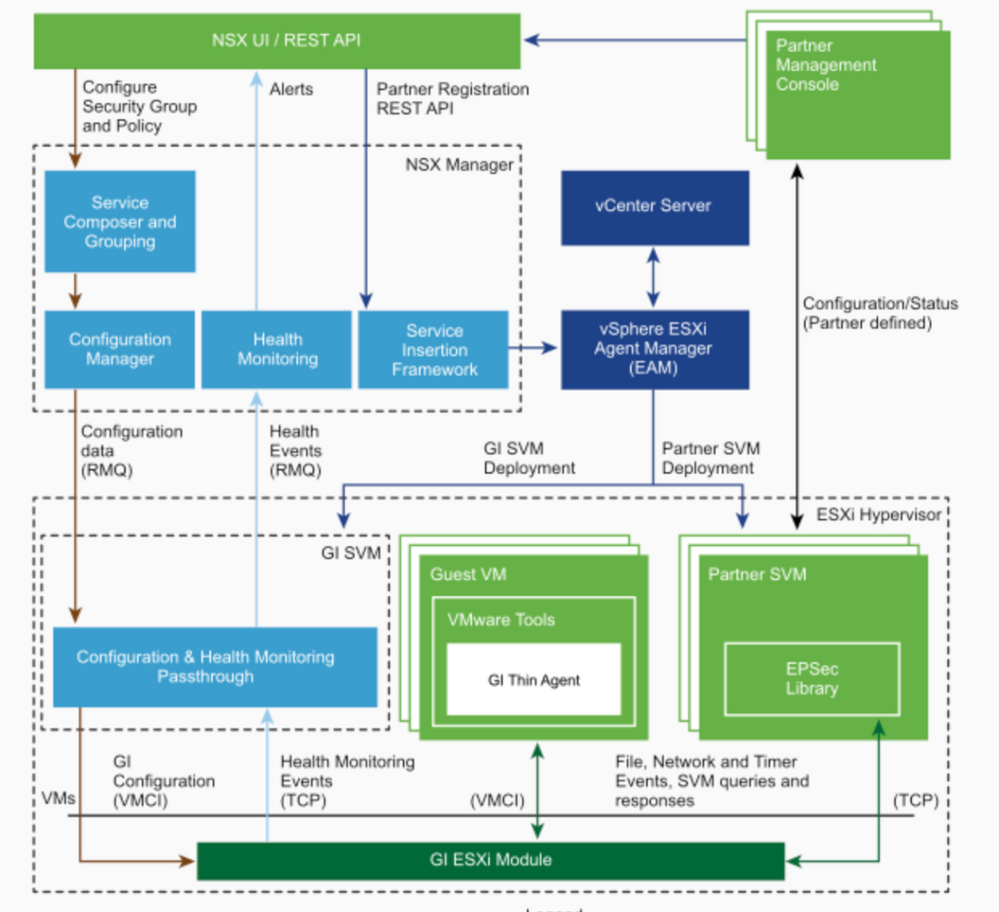
i've read some documents of guest introspection but still don't understand it completely.
my doubts are:
1. the guest introspection is made for anti-virus/malware purpose only?
2. the thin agent driver replaces the traditional AV program in VMs so there's no need to configure antivirus in the VM?
3. is it meaningless to install and use guest introspection without third party's(vmware partners) secure virtual appliances?
4. the thin agent and secure virtual appliance do all the antivirus tasks instead of what typical antivirus programs do?
5. how does it protect offline VMs?
6. is there redundancy between SVMs (since the SVM will be installed on each host in the cluster)?
7. is there any features/functions similar to guest introspection in pure vSphere platform?
sorry for the stupid questions, any reply will be appreciated! ![]()
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
1. the guest introspection is made for anti-virus/malware purpose only?
Yes , the idea is to offloads antivirus and anti-malware agent processing to a dedicated secure virtual appliance which is supported as per VMware interoperability list.
2. the thin agent driver replaces the traditional AV program in VMs so there's no need to configure antivirus in the VM?
Yes, the whole purpose of this architecture is to go with agent less protection . Based on the use case we need to install thin agent driver inside the VM - File Introspection (vsepflt) and Network Introspection (vnetflt) drivers or File introspection driver (Required for Guest introspection)
3. is it meaningless to install and use guest introspection without third party's(vmware partners) secure virtual appliances?
Third party supported per host SVM solution is must . Going via the traditional way of agent based deployment , each agent manage a file of antivirus signatures and perform the scan based on the policy which is certainly not a good fit in a virtualized platform . Inorder to optimize this approach , agent less solution will be a better approach. So better eliminate legacy architecture ![]()
4. the thin agent and secure virtual appliance do all the antivirus tasks instead of what typical antivirus programs do?
Yes, thin agent will monitor the read/write operations inside the guest and notifies the AV solution (Per host SVM) based on the scanning policy and remediation steps we need to take further action if situation demands.
5. how does it protect offline VMs?
Chances of SVM going offline are highly unlikely, but normal virtual machines can certainly go offline . For the machine to remain protected , it has to be online . The moment the status stage from offline to online - Virtual machine will be immediately protected.
6. is there redundancy between SVMs (since the SVM will be installed on each host in the cluster)?
Good question ![]() . You should read this thread -> Guest Introspection dependencies and how to make it highly available
. You should read this thread -> Guest Introspection dependencies and how to make it highly available
7. is there any features/functions similar to guest introspection in pure vSphere platform?
None that I'm aware of
Sree | VCIX-5X| VCAP-5X| VExpert 7x|Cisco Certified Specialist
Please KUDO helpful posts and mark the thread as solved if answered
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
1. the guest introspection is made for anti-virus/malware purpose only?
Yes , the idea is to offloads antivirus and anti-malware agent processing to a dedicated secure virtual appliance which is supported as per VMware interoperability list.
2. the thin agent driver replaces the traditional AV program in VMs so there's no need to configure antivirus in the VM?
Yes, the whole purpose of this architecture is to go with agent less protection . Based on the use case we need to install thin agent driver inside the VM - File Introspection (vsepflt) and Network Introspection (vnetflt) drivers or File introspection driver (Required for Guest introspection)
3. is it meaningless to install and use guest introspection without third party's(vmware partners) secure virtual appliances?
Third party supported per host SVM solution is must . Going via the traditional way of agent based deployment , each agent manage a file of antivirus signatures and perform the scan based on the policy which is certainly not a good fit in a virtualized platform . Inorder to optimize this approach , agent less solution will be a better approach. So better eliminate legacy architecture ![]()
4. the thin agent and secure virtual appliance do all the antivirus tasks instead of what typical antivirus programs do?
Yes, thin agent will monitor the read/write operations inside the guest and notifies the AV solution (Per host SVM) based on the scanning policy and remediation steps we need to take further action if situation demands.
5. how does it protect offline VMs?
Chances of SVM going offline are highly unlikely, but normal virtual machines can certainly go offline . For the machine to remain protected , it has to be online . The moment the status stage from offline to online - Virtual machine will be immediately protected.
6. is there redundancy between SVMs (since the SVM will be installed on each host in the cluster)?
Good question ![]() . You should read this thread -> Guest Introspection dependencies and how to make it highly available
. You should read this thread -> Guest Introspection dependencies and how to make it highly available
7. is there any features/functions similar to guest introspection in pure vSphere platform?
None that I'm aware of
Sree | VCIX-5X| VCAP-5X| VExpert 7x|Cisco Certified Specialist
Please KUDO helpful posts and mark the thread as solved if answered
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great reply from Sreec above - just wanted to add that aside from 3rd party anti-virus products, guest introspection can also be used by the NSX IDFW (Identity Firewall) to determine user login/logoff events. It's not mandatory for IDFW as AD log scraping can also be used, but with the SMB v1 requirement, many people prefer guest introspection for this purpose.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi guys, thank you for the reply,
these answers do help me a lot on understanding the guest introspeciton!
b.t.w
i have 1 more simple question about the guest intro., which is:
how much resource consumption does the guest introspection minimize in guest OS VM?(comparing with using traditional AV programs in the guest.)
is it possible to calculate precisely?
thank you so much![]()
![]()
![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How much resource consumption does the guest introspection minimize in guest OS VM .
I'm unsure about the benchmark testing . However I will be least concerned about it considering traditional AV storms are not going to happen anymore .Saturation can certainly happen since compute and storage is shared ideally in any environment when we have AV engine inside the VM. Few points which I can share are below one's
- We don't own the responsibility of maintaining, patching, and updating antivirus agents , this task is completely offloaded to Appliance - Ease of day to day operational tasks
- AV signature file updates and AV scan engine is also offloaded from VM - Less CPU cycles , less IOPS
- Comparing with a fresh VM with no AV engine ,compute and Storage consumption is certainly less than one which is having AV engine and scanning policy schedules , almost the same performance since we are adding just a vmtool foot print
- Based on the environment, one classic example is VDI. If there is a AV scan required or Virus removal/action required ( we can schedule it in batches ).We need to do it on Master image and eventually on all desktop pools . That is a tedious effort isn't ?
- While the environment keeps scaling as long as underlying vSphere design is perfect , VM performance is guaranteed and most importantly they remain protected without no additional configuration.
Sree | VCIX-5X| VCAP-5X| VExpert 7x|Cisco Certified Specialist
Please KUDO helpful posts and mark the thread as solved if answered
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please consider also the additional overhead of Agentless protection vs. Agent-based
Agentless:
1. You need to install and maintain NSX, Guest Introspection and AV-Vendor Appliance in the right versions (NSX 6.2.4 caused PSOD of the whole host with ESXi < 6.0U2 patch 3 almost daily):
"Cause
PSOD occurs due to race condition in dvfilter vmci socket deregistration. A small window existed in which function pointers are NULLed out but we haven't actually deregistered the socket callback."
2. You need VMware Tools in the right version (wrong version will give very slow performance) "Slow VMs after upgrading VMware tools in NSX/ vCloud Networking and Security (2144236)."
3. If you do not have NSX Advanced (~4k$/Socket) you cannot use network introspection and should not install the NSX Network Introspection Driver, as this driver also has caused bluescreens in windows in the past even when not used
So you need:
- AV Manager
- NSX Manager
- Guest Introspection VM
- AV VM
- VMware Tools with NSX GI Driver
And everything has to work for your VMs to be protected (Fail-Open).
There was also a Problem in NSX up to 6.4.0 where the epsecmux on the Guest Introspection VM would crash from time to time and you had to restart the GI machine to get it working again
Also there will be cases where one of the components has a problem but you will not be able to see that your AV is not working except when testing with eicar
vs.
- AV Manager
- AV Agent
Conclusion:
Just make very sure that you REALLY can profit from the advantages. So either VDI with a very high number of VMs per host or you already use NSX Advanced and you want to agentless protect (AV and IPS) your customer-managed VMs where you cannot install an agent.
We use agentless Anti-malware and have been bitten by all the problem and bugs described in the last one and a half year.